Continuous Threat Exposure Nonstop Danger Openness The executives (CTEM) addresses a proactive and dynamic way to deal with defending computerized resources in the present steadily developing danger scene. In a period where cyberattacks are progressively complex and constant, associations face mounting strain to brace their guards and moderate weaknesses successfully. CTEM arises as a far reaching system that empowers associations to ceaselessly screen, survey, and answer possible dangers continuously, subsequently lessening openness to digital dangers and guaranteeing the flexibility of their computerized foundation. At its center, CTEM incorporates a comprehensive methodology that coordinates state of the art innovations, hearty cycles, and proactive measures to distinguish, break down, and remediate dangers across all layers of the IT climate. By utilizing progressed danger knowledge, AI calculations, and computerization abilities, CTEM engages security groups to remain one stride in front of enemies, expect to arise dangers, and make a precautionary move to safeguard basic resources and delicate information. Besides, CTEM encourages a culture of cooperation and data sharing, empowering associations to use aggregate experiences and mastery to reinforce their security pose cooperatively. As associations keep on standing up to developing digital dangers, CTEM arises as a urgent structure that empowers them to adjust, improve, and flourish notwithstanding misfortune, protecting their computerized resources and saving confidence in an undeniably interconnected world.In the consistently developing scene of network safety, associations face an undeniably perplexing exhibit of dangers that require steady carefulness and proactive measures to relieve. Enter Ceaseless Danger Openness The board (CTEM), a powerful methodology that changes how associations identify, dissect, and answer security dangers continuously. At its center, CTEM is an exhaustive structure intended to furnish associations with consistent perceivability into their threatening statement scene, empowering them to recognize weaknesses, survey chances, and focus on remediation endeavors successfully.

Implement A Continuous Threat Exposure Management (ctem) Program
Executing a Persistent Danger Openness The board (CTEM) program is fundamental in the present network safety scene to safeguard associations from developing dangers and weaknesses. The most important phase in executing a CTEM program is to direct a complete evaluation of the association’s ongoing security act, including framework, frameworks, applications, and information resources. This appraisal recognizes existing weaknesses and likely weak spots that should be tended to. Whenever weaknesses are distinguished, associations can focus on remediation endeavors in light of chance seriousness and likely effect. Carrying out robotized weakness examining apparatuses can smooth out this cycle, giving constant perceivability into the association’s aggressive statement scene and empowering continuous location of weaknesses. Also, associations ought to lay out clear arrangements and strategies for overseeing security episodes and answering dangers immediately. This incorporates characterizing jobs and obligations, laying out correspondence channels, and carrying out episode reaction intends to guarantee a planned and powerful reaction to security occurrences. Moreover, representative preparation and mindfulness programs assume a urgent part in the progress of a CTEM program, as human blunder stays one of the main sources of safety breaks. By teaching representatives about normal network protection dangers and best practices for moderating dangers, associations can engage their labor force to become proactive safeguards against digital dangers. At long last, customary observing, testing, and assessment are fundamental parts of a fruitful CTEM program. Constantly observing the adequacy of safety controls, testing episode reaction methods through reenactments, and directing standard security reviews assist with guaranteeing that the association’s guards stay powerful and versatile to arising dangers. Generally speaking, executing a CTEM program requires an all encompassing and proactive way to deal with network safety, coordinating individuals, cycles, and innovation to successfully oversee and relieve dangers in the present unique danger scene.
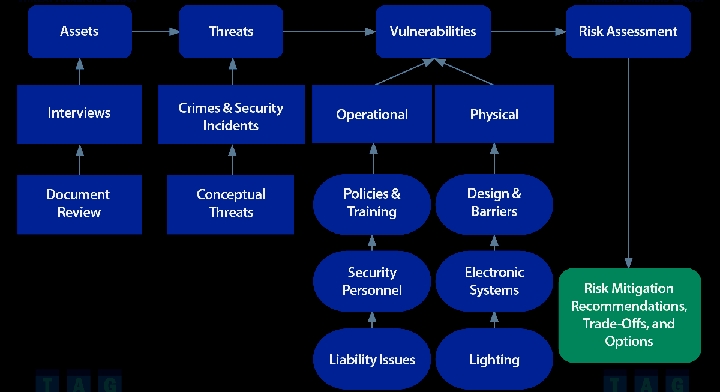
How To Mitigate Threats
Moderating dangers is an essential part of guaranteeing the security and flexibility of an association’s tasks, resources, and partners. The most vital phase in moderating dangers is to direct an exhaustive gamble evaluation to recognize likely dangers and weaknesses that could present dangers to the association. Once distinguished, associations can focus on dangers in light of their probability and expected influence, permitting them to assign assets really to address the most basic dangers first. Alleviation methodologies might shift relying upon the idea of the danger, however normal methodologies incorporate carrying out specialized controls like firewalls, encryption, and access controls to forestall unapproved admittance to frameworks and information. Moreover, associations can execute security mindfulness preparing projects to teach workers about normal network safety dangers and best practices for moderating dangers. Moreover, laying out episode reaction plans and methodology empowers associations to answer quickly and really to security occurrences, limiting their effect and reestablishing ordinary activities as fast as could be expected. Coordinated effort with industry peers, government organizations, and network safety specialists can likewise give important experiences and assets to alleviating dangers actually. Also, normal checking, testing, and refreshing of safety efforts are fundamental to guarantee their viability and versatility to developing dangers. By taking on a proactive and multifaceted way to deal with danger relief, associations can decrease their openness to chances and fortify their general security act, consequently defending their tasks and notoriety in an undeniably mind boggling and dynamic danger scene.

Continuous Risk Management Process
The Persistent Gamble The board Cycle (CRMP) addresses a proactive way to deal with overseeing takes a chance in an association’s tasks, projects, and key drives. At its center, CRMP is a deliberate and progressing process that includes recognizing, evaluating, focusing on, and moderating dangers to accomplish hierarchical targets while limiting likely adverse consequences. The cycle starts with the recognizable proof of dangers through exhaustive examination of inner and outer variables, remembering changes for the business climate, innovative progressions, administrative prerequisites, and arising dangers. Whenever chances are recognized, they are evaluated in light of their probability and possible effect on the association’s objectives, assets, and partners. This evaluation focuses on chances, permitting associations to zero in their assets on tending to the most basic dangers first. Relief techniques are then evolved and carried out to lessen the probability or effect of recognized chances, which might incorporate gamble evasion, risk move, risk alleviation, or hazard acknowledgment. Besides, CRMP accentuates the significance of persistent checking and survey to guarantee that risk the board systems stay compelling and lined up with the association’s goals and developing gamble scene. By taking on a consistent gamble the board approach, associations can expect and adjust to changes all the more really, limit disturbances, and jump all over chances for development and development while keeping up with versatility notwithstanding vulnerability. Generally, CRMP fills in as an essential device for associations to explore the intricacies of the cutting edge business climate and make supportable progress in a steadily impacting world.

External Techniques Of Exposure Management
Outer procedures of openness the board allude to systems and practices utilized by associations to moderate dangers emerging from factors outside their nearby control, like international occasions, monetary variances, administrative changes, and inventory network disturbances. These methods include proactive measures pointed toward recognizing, evaluating, and answering outer dangers and weaknesses that can possibly affect the association’s activities, notoriety, and main concern. One normal outside method is situation arranging, which includes breaking down different speculative situations and their likely effects on the association, considering better readiness and flexibility notwithstanding vulnerability. Another method is partner commitment, which includes constructing and keeping up with associations with key partners, like government offices, industry affiliations, and local area associations, to remain informed about outside improvements and team up on risk relief endeavors. Also, associations might use risk move systems, like protection and legally binding arrangements, to move specific dangers to outsiders, in this way diminishing their openness to monetary misfortunes. Besides, outside methods of openness the board might incorporate broadening of providers and markets, which mitigates the gamble of interruptions brought about by conditions on a solitary provider or market section. By and large, by utilizing outer methods of openness the board, associations can upgrade their capacity to expect, alleviate, and adjust to outside dangers and vulnerabilities, in this manner protecting their drawn out progress and manageability in an undeniably unpredictable and interconnected world.

Security Risk Mitigation Plan Examples
Security risk moderation plans are fundamental parts of any association’s network safety system, giving an organized way to deal with distinguishing, surveying, and tending to expected dangers and weaknesses. One illustration of a security risk relief plan is carrying out vigorous access controls to forestall unapproved admittance to delicate information and frameworks. This might incorporate carrying out multifaceted confirmation, job based admittance controls, and customary reviews of client authorizations to guarantee that main approved people approach basic assets. Another model is carrying out encryption conventions to safeguard information both very still and on the way, lessening the gamble of information breaks and unapproved capture. Moreover, associations can convey interruption identification and avoidance frameworks to screen network traffic for dubious action and naturally block or ready executives to potential security dangers. Moreover, ordinary security mindfulness preparing programs for workers can assist with alleviating the gamble of social designing assaults, phishing tricks, and other human-related security weaknesses. Besides, laying out an extensive occurrence reaction plan that frames jobs, obligations, and methodology for answering security episodes is basic for limiting the effect of breaks and reestablishing ordinary tasks quickly. By executing a blend of specialized controls, preparing projects, and occurrence reaction conventions, associations can successfully moderate security dangers and improve their general online protection pose, defending their resources, tasks, and notoriety from a great many dangers.

AI-Augmented Development in the Digital Era